sFlow in Fortigate disables Hardware Acceleration
Do not use sFlow in Fortigate - use Netflow instead
I was approached last month by 2 unrelated Fortigate admins with the same
problem - slow performance of otherwise very beafy Fortigate models. After some
digging in the configuration the culprit was found - there was enabled on WAN
interface sFlow. sflow collects passing traffic statistics and sends it to
external server. What everybody nowadays does with Netflow. But back in the days
sFlow was the first available, quite popular, but … it was in the late 90s.
HP that invented it in 1991 made it available on all their switches ever since.
Fortinet introduced sFlow capability in FortiOS 4, I even wrote a post about it
Do not miss the long awaited addition to the Fortigate 4 MR2 – sFlow data export
which happened in 2010. The problem with sFlow is that on Fortigate models
with Network Processor (NP) acceleration chip, it disables hardware acceleration
for the traffic
on the interfaces it was enabled on. Not good, at all.
So, the takeaway - use Netflow if you need to, not sFlow.
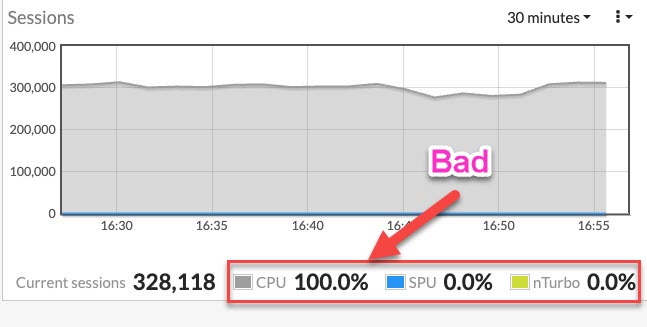
The graph below shows that 100% of network traffic (it does NOT show how CPU itself is loaded, fortunately) is being processed by CPU instead on the NP ASIC, which causes lowered network performance:
Official Fortinet docs telling just that: sFlow and NetFlow and hardware acceleration
-
If you toubleshoot Fortigate and other gear in your work, make sure to clone my Fortigate and other vendors' debug commands cheat sheets
Follow me on https://www.linkedin.com/in/yurislobodyanyuk/ not to miss what I publish on Linkedin, Github, blog, and more.