Fortigate DLP file filtering and more examples
- Important facts
- Block downloading PDF and MP4 files (FortiOS up to 7.2.4)
- File Filter (all versions of FortiOS, no lic needed)
- Block uploading/downloading documents containing SSN or/and Credit Card numbers (7.2.4 or newer)
- Block file uploads/downloads when file is an Office file and contains SSN or any file larger than 10K
- Debug
Important facts
-
Requires SSL Deep Inspection to be used.
-
Starting with FortiOS 7.4.x DLP is a licensed feature, free is only File Filter (may change any minute).
-
Archival preserves ALL matched DLP sensor traffic including contents of files/emails, but requires Fortigate with a harddisk.
-
Archiving requires proxy-based sensor/policy.
-
Feature visibility: DLP was removed from GUI in 6.4, 7.0, then returned in recent versions, BUT it is always available in CLI configuration.
-
Starting 7.2.4 configuration commands changed, new ones added - more granularity, more options.
Block downloading PDF and MP4 files (FortiOS up to 7.2.4)
There are pre-defined file types in Fortigate, PDF being one of them, so as the 1st filtering condition I will use file-type pdf. This way DLP will look at files meta-data, regardless of their extensions. But for the .mp4 files there is no such pre-defined file type, so I will have to block it by filename pattern using *.mp4, which is less secure as it is enough for file extension to be changed to something else and Fortigate will not block it.
config dlp filepattern
edit 3 <-- THIS NUMBER IS USED IN SENSOR
set name "PDFandMPEG"
config entries
edit "PDF"
set filter-type type
set file-type pdf
next
edit "MPEG"
set filter-type type
set file-type mpeg
next
edit "*.mp4" <-- PATTERN IN FILE NAME TO LOOK FOR
next
end
next
end
config dlp sensor
edit "PDF_MPEG_sensor"
config filter
edit 1
set proto http-get http-post ftp
set filter-by file-type
set file-type 3 <-- THIS IS POLICY ID SEE ABOVE
set action block
next
end
next
end
-
Security rule using the DLP sensor:
config firewall policy
edit 138
set srcintf "Dialup3"
set dstintf "VDOM_EXT"
set action accept
set srcaddr "all"
set dstaddr "all"
set schedule "always"
set service "ALL"
set utm-status enable
set ssl-ssh-profile "deep-inspection"
set dlp-sensor "PDF_MPEG_sensor"
set logtraffic all
set nat enable
next
end
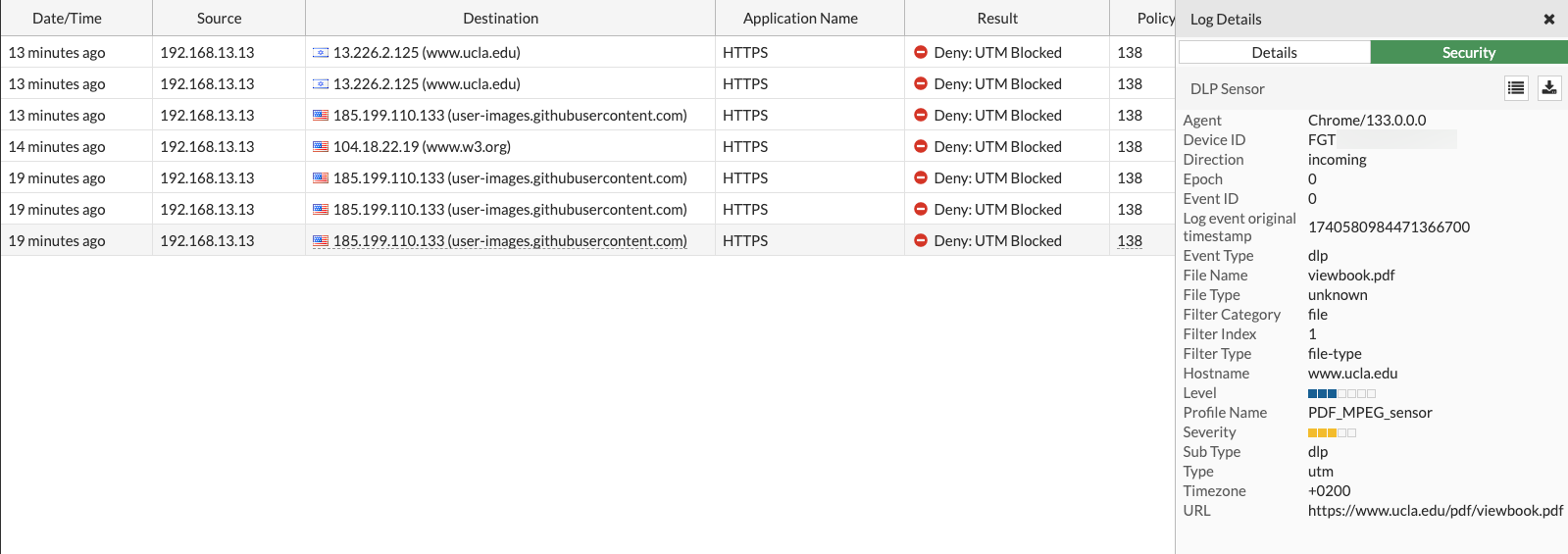
In Forward logs the block is seen as (I tried accessing PDF file on UCLA website):
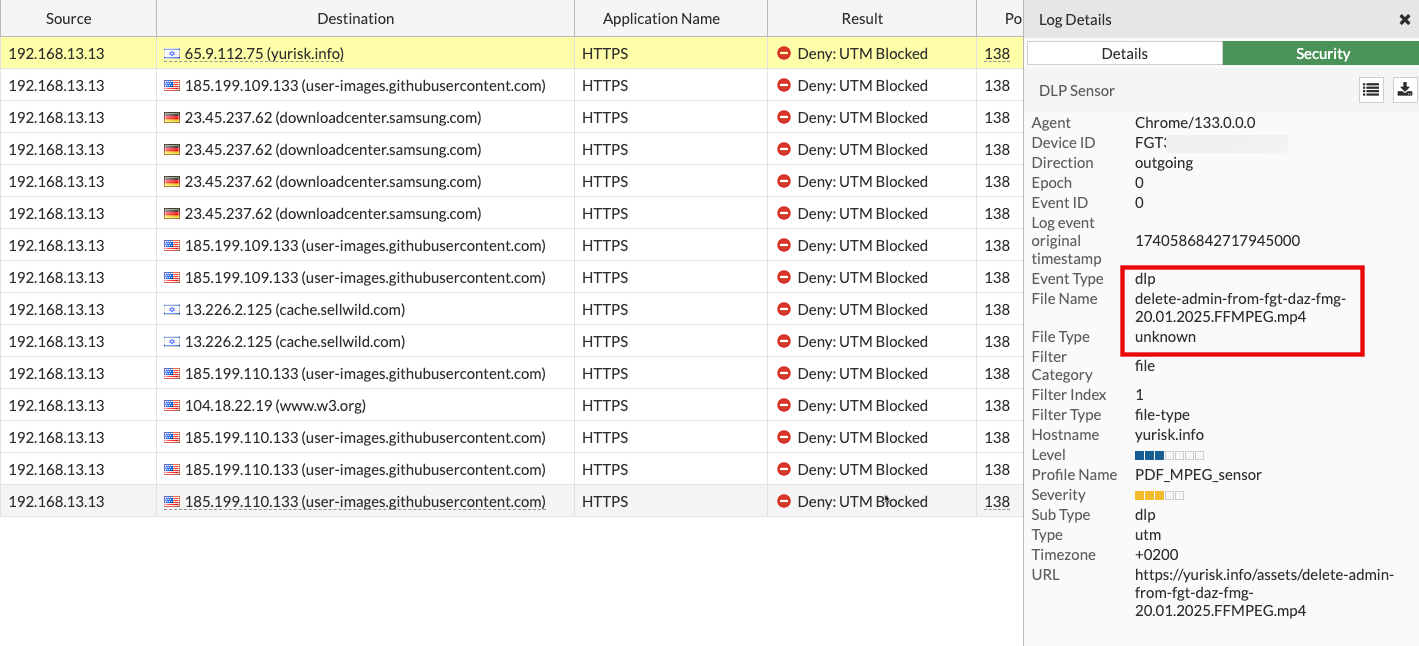
The MP4 file block by the file name pattern is seen as:
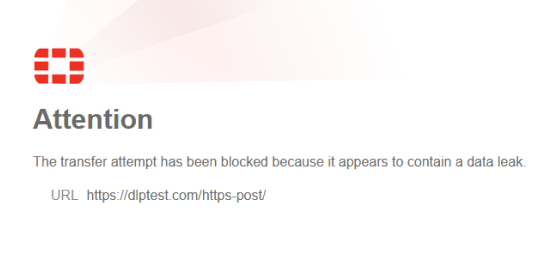
To the end user, the block message will look:
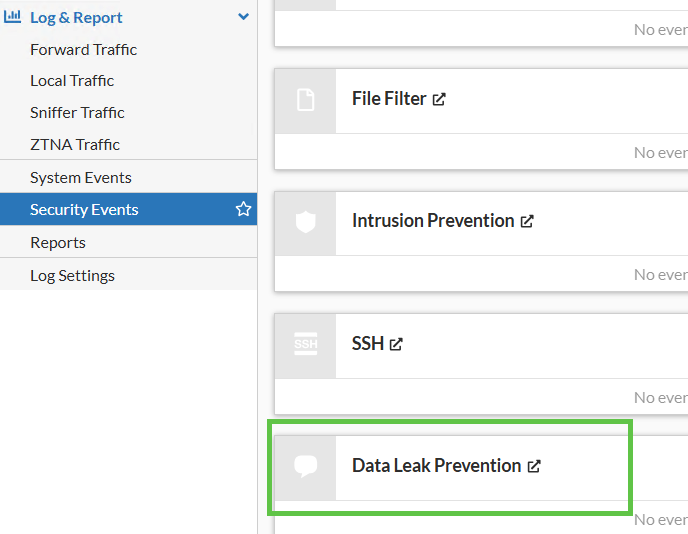
DLP logs are located inside Security Events:
|
Note
|
I run all tests with the help of the website https://dlptest.com/https-post/ |
File Filter (all versions of FortiOS, no lic needed)
File Filter is a dumbed-down version of DLP that does NOT require a DLP license. It allows us to pick from a list of predefined file types and either block or log them. Also we can choose what protocols to look at: http/ftp/pop3/etc. List of supported file types: https://docs.fortinet.com/document/fortigate/7.4.5/administration-guide/610893 .
File Filter does NOT allow blocking by file sizes or patterns/regex inside file content. It is available in GUI.
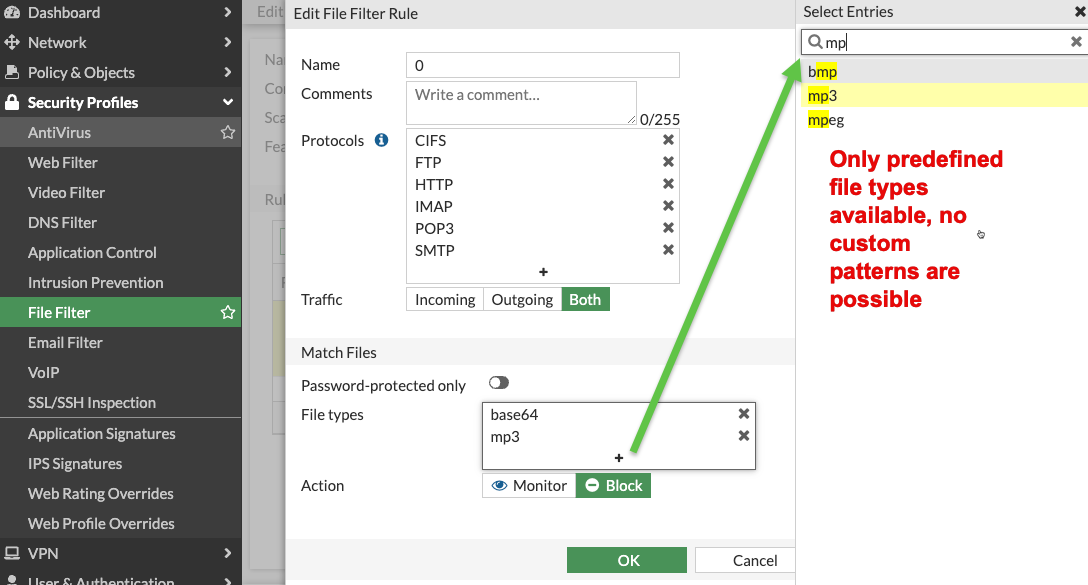
Fortigate up to 7.2.4
-
File type to match:
config dlp filepattern
edit 4
set name "blockMP3"
config entries
edit "MP3"
set filter-type type
set file-type mp3
next
end
next
end
-
DLP sensor combining the above file pattern with protocols to check, and action - block:
config dlp sensor
edit "MP3block"
config filter
edit 1
set proto http-get http-post ftp
set filter-by file-type
set file-type 4
set action block
next
end
next
end
-
(FortiOS up to 7.2.4) Security rule using DLP sensor and file-filter:
config firewall policy
edit 138
set srcintf "Dialup3"
set dstintf "VDOM_EXT"
set action accept
set srcaddr "all"
set dstaddr "all"
set schedule "always"
set service "ALL"
set utm-status enable
set ssl-ssh-profile "deep-inspection"
set dlp-sensor "MP3block"
set logtraffic all
set nat enable
next
end
Fortigate 7.2.4 or newer
-
Set up file-filter profile
config file-filter profile
edit "MP3block"
config rules
edit "MP3typeblock"
set protocol http ftp smtp
set action block
set file-type "mp3"
next
end
next
end
-
Use this profile directly in the security rule:
config firewall policy
edit 9
set uuid 6d0debbe-1755-51ef-ca7d-d938a76591a0
set srcintf "Peer1P1"
set dstintf "NV5000-EXT"
set action accept
set srcaddr "Peer1pool"
set dstaddr "all"
set schedule "always"
set service "ALL"
set utm-status enable
set inspection-mode proxy
set ssl-ssh-profile "deep-inspection"
set dlp-profile "BlockSSNCCprofile"
set file-filter-profile "MP3block"
set logtraffic all
set nat enable
set users "yurisk1"
next
end
Block uploading/downloading documents containing SSN or/and Credit Card numbers (7.2.4 or newer)
FortiOS 7.2.4 added more granularity in matching the content - we now have predefined signatures for Social Security Numbers (SSN), Credit card numbers, and can also search contents of the files for regex or hex string matches.
The flow changed as well:
-
Create dictionary referencing built-in data types and setting match criteria.
-
Create DLP sensor referencing dictionary(s) and adding matching conditions (e.g. how many times to match).
-
Create DLP profile, referencing DLP sensor and setting action, then use this DLP profile in the security policy.
Built-in data types (on what to match)
We have the follwoing data types to be natched on. While we can edit definitions here, I don’t see any reason to do so:
config dlp data-type
edit "g-credit-card"
set pattern "\\b([2-6]{1}\\d{3})[- ]?(\\d{4})[- ]?(\\d{2})[- ]?(\\d{2})[- ]?(\\d{2,4})\\b"
set verify "built-in"
set look-back 20
set transform "\\b\\1[- ]?\\2[- ]?\\3[- ]?\\4[- ]?\\5\\b"
next
edit "g-hex"
set pattern "built-in"
next
edit "g-keyword"
set pattern "built-in"
next
edit "g-mip-label"
set pattern "^[[:xdigit:]]{8}-[[:xdigit:]]{4}-[[:xdigit:]]{4}-[[:xdigit:]]{4}-[[:xdigit:]]{12}$"
set transform "built-in"
next
edit "g-regex"
set pattern "built-in"
next
edit "g-ssn-us"
set pattern "\\b(\\d{3})-(\\d{2})-(\\d{4})\\b"
set verify "(?<!-)\\b(?!666|000|9\\d{2})\\d{3}-(?!00)\\d{2}-(?!0{4})\\d{4}\\b(?!-)"
set look-back 12
set transform "\\b\\1-\\2-\\3\\b"
next
end
Let’s create dicitonary referencing SSN/Credit cards built-ins:
config dlp dictionary
edit "SSNCCdict"
config entries
edit 1
set type "g-credit-card" <-- BUILT-INs SEE ABOVE
next
edit 2
set type "g-ssn-us"
next
end
next
end
-
Create DLP sensor:
config dlp sensor
edit "blockSSNCC"
set match-type match-any <-- THIS DEFAULT SO WILL NOT APPEAR
config entries
edit 1
set dictionary "SSNCCdict"
set count 1 <-- DEFAULT SO WILL NOT APPEAR
next
end
next
end
-
Now, create DLP profile:
config dlp profile (profile) $ edit BlockSSNCCprofile new entry 'BlockSSNCCprofile' added (BlockSSNCCprofile) $ set comment Comment. feature-set Flow/proxy feature set. replacemsg-group Replacement message group used by this DLP profile. dlp-log Enable/disable DLP logging. extended-log Enable/disable extended logging for data leak prevention. nac-quar-log Enable/disable NAC quarantine logging. full-archive-proto Protocols to always content archive. summary-proto Protocols to always log summary. (BlockSSNCCprofile) $ config rule (rule) $ edit 0 new entry '0' added (0) $ set name Filter name. severity Select the severity or threat level that matches this filter. type Select whether to check the content of messages (an email message) or files (downloaded files or email attachments). proto Check messages or files over one or more of these protocols. filter-by Select the type of content to match. file-size Match files this size or larger (0 - 4294967295 kbytes). file-type Select the number of a DLP file pattern table to match. action Action to take with content that this DLP profile matches. (0) $ set action allow Allow the content to pass through the FortiGate and do not create a log message. log-only Allow the content to pass through the FortiGate, but write a log message. block Block the content and write a log message. quarantine-ip Quarantine all traffic from the IP address and write a log message. (0) $ set action block (0) $ set type file // OR message FOR EMAILS (0) $ set filter-by sensor Use DLP sensors to match content. encrypted Look for encrypted files. none No content scan. (0) $ set filter-by sensor (0) $ set sensor "blockSSNCC"
Final version:
config dlp profile
edit "BlockSSNCCprofile"
config rule
edit 1
set proto http-get http-post ftp
set filter-by sensor
set sensor "blockSSNCC"
set action block
next
end
next
end
-
Finally, apply UTM, SSL Deep inspection, and DLP profile in the security rule:
config firewall policy
edit 9
set srcintf "Peer1P1"
set dstintf "VMVDOM-EXT"
set action accept
set srcaddr "Peer1pool"
set dstaddr "all"
set schedule "always"
set service "ALL"
set utm-status enable
set ssl-ssh-profile "deep-inspection"
set dlp-profile "BlockSSNCCprofile"
set logtraffic all
set nat enable
set users "yurisk1"
next
end
The block in logs:
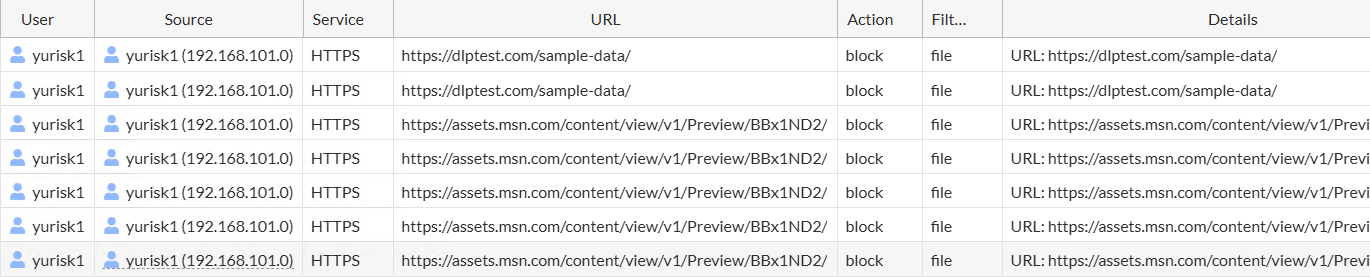
Block file uploads/downloads when file is an Office file and contains SSN or any file larger than 10K
We can combine all matching conditions: data-type, file size, and file type
-
Search for Office files:
config dlp filepattern
edit 3
set name "OfficeDocs"
config entries
edit "OFFICE"
set filter-type type
set file-type msoffice
next
edit "OFFICEX"
set filter-type type
set file-type msofficex
next
end
next
end
-
Search for SSNs in contents:
config dlp sensor
edit "blockSSNCC"
config entries
edit 1
set dictionary "SSNCCdict"
next
end
next
end
-
Final DLP profile to combine the 2 conditions:
config dlp profile
edit "OFFICEandSIZE"
config rule
edit 1
set proto http-get http-post ftp
set file-size 10
set action block
next
edit 2
set severity high
set proto http-get http-post ftp
set filter-by sensor
set file-type 3
set sensor "blockSSNCC"
set action block
next
end
next
end
-
And, finally - apply to security policy:
config firewall policy
edit 9
set srcintf "Peer1P1"
set dstintf "VMVDOM-EXT"
set action accept
set srcaddr "Peer1pool"
set dstaddr "all"
set schedule "always"
set service "ALL"
set utm-status enable
set ssl-ssh-profile "deep-inspection"
set dlp-profile "OFFICEandSIZE"
set logtraffic all
set nat enable
set users "yurisk1"
next
end
Debug
For flow-based sensors (warning: a lot of output):
diagnose ips filter set "host <Source or destination IP address >" diagnose ips debug enable all diagnose debug enable
For proxy-based dlp sensors:
diagnose sys scanunit debug all -OR- diag sys scanunit debug dlp diag wad debug enable category scan diagnose debug enable
I also write cheat sheets/scripts/guides to help in daily work, so make sure to check out my Github at https://github.com/yuriskinfo and https://www.linkedin.com/in/yurislobodyanyuk/