yurisk.info
Yuri Slobodyanyuk's blog on IT Security and Networking sharing experience and expertise
Category: Cisco (page 1 of 6)
Useful CLI commands for Cisco CUCM .
I don’t work on the command line of CUCM often, if ever – you may add, but when the need arises here is the short list of commands to keep. A little reminder – the latest (starting version 5 and on) of Cisco CUCM software is Linux (namely Red Hat) based, which of course includes the terminal access – be it a physical via console or a network one over ssh .
You create a username/password for the terminal during the CUCM installation.
As Cisco do not want us to mess with the underlying OS, our interaction is limited to a very restricted kind of shell . So you don’t have access to the Linux commands, but you do have a predefined set of CUCM commands of which I present most useful ones here.
I run the examples below on a MCS hardware server so your output may vary.
– Changing password for yourself/another user . Know that it is here, but do not play with it risking to lock yourself out of the server.
admin:set password { age* | complexity* | expiry* | inactivity* | user* }
– Get the disk usage
show diskusage activelog
– Show the status of the fans (irrelevant for VMware based install)
admin:show environment fans
(RPMS) Lower Critical
ID Current Threshold Status
Fan Sensor 1 7800 4200 OK
Fan Sensor 2 7950 4200 OK
Fan Sensor 3 7800 4200 OK
Fan Sensor 4 7350 4200 OK
Fan Sensor 5 7200 4200 OK
– Show the server temperature (irrelevant for VMware based install)
show environment temperatures
(Celcius) Non-Critical Critical Threshold Threshold
ID Current Lower Upper Lower Upper Location Temperature Sensor
1 24 53 54 55 62 1
– Show the server hardware (irrelevant for VMware based install)
show hardware
HW Platform : 7825I4
Processors : 1
Type : Intel(R) Core(TM)2 Duo CPU E8400 @ 3.00GHz
CPU Speed : 3000
Memory : 2048 MBytes
show logins
administ pts/0 192.168.7.1 Wed Aug 12 09:56 still logged in
– Show physical memory (irrelevant for VMware based install)
show memory modules
Bank Locator Size Active Status
DIMM 1 DIMM 1 1024 MB TRUE OK
DIMM 3 DIMM 3 1024 MB TRUE OK
– Show interface status (more useful for hardware based servers than VMware ones)
show network eth0
Ethernet 0
DHCP : disabled Status : up
IP Address : 192.168.10.1 IP Mask : 255.255.255.000
Link Detected: yes Mode : Auto enabled, Full, 100 Mbits/s
Duplicate IP : no
DNS Not configured.
Gateway : 192.168.10.254 on Ethernet 0
– Show number of open connections . If there is some network connectivity issue this number will be unusually low as each IP Phone/voice gateway is counted as a connection.
show network ip_conntrack
972
– Show open and accessible over the network ports
show network ipprefs public
Application IPProtocol PortValue Type XlatedPort Status Description
———— ———— ———— ———— ———— ———— ————
sshd tcp 22 public – enabled sftp and ssh access
clm udp 8500 public – enabled cluster manager
clm tcp 8500 public – enabled cluster manager
tomcat tcp 8443 translated 443 enabled secure web access
tomcat tcp 8080 translated 80 enabled web access
ntpd udp 123 public – enabled network time sync Continue reading
ip access-list extended OUTBOUND permit tcp any any reflect MIRROR permit udp any any reflect MIRROR permit icmp any any reflect MIRRORThen the access-list to put on external facing interface inbound:
ip access-list extended INBOUND evaluate MIRRORAnd finally apply it:
#conf t (config)# interface FastEthernet 0/1 (config-if)# ip access-group OUTBOUND out (config-if)# ip access-group INBOUND inDo not forget of course its drawbacks:
- It does not work well with complex protocols like FTP
- It is not exactly stateful - what happens is that router dynamically adds non-stateful entries in INBOUND access list that mirror the passing traffic, expiring it after some time. In doing so Cisco router looks only on destination/source IP address and port.
Once it was a nice-to-have configuration that most ISPs in the world ignored anyway, but today it is a must if you are planning to advertise your networks via BGP through your uplink provider – your route object in the AS whois database of the uplink provider. If not – you will happily advertise your networks, the uplink provider will duly advertise them to its uplink peers, which will check AS registry database of your provider and not finding this route object will silently drop the advertising.
Of course it is duty of your transit ISP provider to update their records with your network, but after all, you are the one most interested – so as they say in Russian ” Доверяй но проверяй ” , and here is how to do it:
whois -h whois.ripe.net — ‘-a -r -i or -T route AS1680’ | grep route
In this example I assume your uplink provider is Netvision with AS1680 , replace AS number with the correct one.
Output will look like:
route: 109.186.0.0/16
route: 109.253.0.0/16
route: 117.121.245.0/24
route: 138.134.0.0/16
route: 147.161.0.0/16
…
If you don’t find in such listing your network – Houston, you have a problem here.
Yesterday I had to extract some data from a CDR report for a client, namely call start time, its duration and the called number. And while I am sure Google has zillion scripts to be found, it was much faster to hack this one-liner .
The script extracts the following fields from the CDR report in this order:
dateTimeOrigination – for outgoing calls it is the time the device goes off hook
callingPartyNumber – initiator of the call
finalCalledPartyNumber – the reached/dialed number (after forwarding if any)
duration – duration of the call
The extracted data is placed in CSV format to be easily imported into Microsoft Excel.
Enjoy. Any questions – feel free to ask here.
[bash] awk -F, ‘BEGIN {OFS=","} {print strftime("%c",$5),$9,$31,$56}’ report_cdr [/bash]
Output:
Sun 04 May 2014 01:54:37 PM IDT,0555555555,2988,41
Sun 04 May 2014 01:55:07 PM IDT,2908,0555555555,25
In case you want to extract some other fields from CDR , here is the full list of available values and their position. For explanation you can look here – Cisco Call Detail Records Field Descriptions
1 cdrRecordType
2 globalCallID_callManagerId
3 globalCallID_callId
4 origLegCallIdentifier
5 dateTimeOrigination
6 origNodeId
7 origSpan
8 origIpAddr
9 callingPartyNumber
10 callingPartyUnicodeLoginUserID
11 origCause_location
12 origCause_value
13 origPrecedenceLevel
14 origMediaTransportAddress_IP
15 origMediaTransportAddress_Port
16 origMediaCap_payloadCapability
17 origMediaCap_maxFramesPerPacket
18 origMediaCap_g723BitRate
19 origVideoCap_Codec
20 origVideoCap_Bandwidth
21 origVideoCap_Resolution
22 origVideoTransportAddress_IP
23 origVideoTransportAddress_Port
24 origRSVPAudioStat
25 origRSVPVideoStat
26 destLegIdentifier
27 destNodeId
28 destSpan
29 destIpAddr
30 originalCalledPartyNumber
31 finalCalledPartyNumber
32 finalCalledPartyUnicodeLoginUserID
33 destCause_location
34 destCause_value
35 destPrecedenceLevel
36 destMediaTransportAddress_IP
37 destMediaTransportAddress_Port
38 destMediaCap_payloadCapability
39 destMediaCap_maxFramesPerPacket
40 destMediaCap_g723BitRate
41 destVideoCap_Codec
42 destVideoCap_Bandwidth
43 destVideoCap_Resolution
44 destVideoTransportAddress_IP
45 destVideoTransportAddress_Port
46 destRSVPAudioStat
47 destRSVPVideoStat
48 dateTimeConnect
49 dateTimeDisconnect
50 lastRedirectDn
51 pkid
52 originalCalledPartyNumberPartition
53 callingPartyNumberPartition
54 finalCalledPartyNumberPartition
55 lastRedirectDnPartition
56 duration
57 origDeviceName
58 destDeviceName
59 origCallTerminationOnBehalfOf
60 destCallTerminationOnBehalfOf
61 origCalledPartyRedirectOnBehalfOf
62 lastRedirectRedirectOnBehalfOf
63 origCalledPartyRedirectReason
64 lastRedirectRedirectReason
65 destConversationId
66 globalCallId_ClusterID
67 joinOnBehalfOf
68 comment
69 authCodeDescription
70 authorizationLevel
71 clientMatterCode
72 origDTMFMethod
73 destDTMFMethod
74 callSecuredStatus
75 origConversationId
76 origMediaCap_Bandwidth
77 destMediaCap_Bandwidth
78 authorizationCodeValue
79 outpulsedCallingPartyNumber
80 outpulsedCalledPartyNumber
81 origIpv4v6Addr
82 destIpv4v6Addr
83 origVideoCap_Codec_Channel2
84 origVideoCap_Bandwidth_Channel2
85 origVideoCap_Resolution_Channel2
86 origVideoTransportAddress_IP_Channel2
87 origVideoTransportAddress_Port_Channel2
88 origVideoChannel_Role_Channel2
89 destVideoCap_Codec_Channel2
90 destVideoCap_Bandwidth_Channel2
91 destVideoCap_Resolution_Channel2
92 destVideoTransportAddress_IP_Channel2
93 destVideoTransportAddress_Port_Channel2
94 destVideoChannel_Role_Channel2
95 incomingProtocolID
96 incomingProtocolCallRef
97 outgoingProtocolID
98 outgoingProtocolCallRef
99 currentRoutingReason
100 origRoutingReason
101 lastRedirectingRoutingReason
102 huntPilotDN
103 huntPilotPartition
104 calledPartyPatternUsage
105 outpulsedOriginalCalledPartyNumber
106 outpulsedLastRedirectingNumber
107 wasCallQueued
108 totalWaitTimeInQueue
109 callingPartyNumber_uri
110 originalCalledPartyNumber_uri
111 finalCalledPartyNumber_uri
112 lastRedirectDn_uri
113 mobileCallingPartyNumber
114 finalMobileCalledPartyNumber
115 origMobileDeviceName
116 destMobileDeviceName
117 origMobileCallDuration
118 destMobileCallDuration
119 mobileCallType
120 originalCalledPartyPattern
121 finalCalledPartyPattern
122 lastRedirectingPartyPattern
123 huntPilotPattern
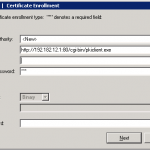
If you didn’t notice Cisco IOS routers can serve as CA servers as well. The example configurations are easy to find on the cisco.com but the only trick to know when enrolling Cisco VPN client with IOS CA is the syntax you put as url – the string should look:
http://192.182.12.1:80/cgi-bin/pkiclient.exe
I attach below screenshot so you can see what I mean.
Some references as well .
ieoc.com/forums/t/12071.aspx
To continue the series I did this video of configuring users to manage IPS sensor – adding/deleting/resetting password/unlocking them. All the configs are being done on CLI.
Some great products get unfair treatment for unclear reasons. One such gear is Cisco IPS sensor 4200 appliance, that while doing its job doesn’t get much attention, fame and even worse proper relation on Cisco.com documentation site. The documentation exists but scarce , examples of configuration – close to none, screenshots – go find. You got the picture – and here comes my humble effort to introduce the sensor to wider audience of this website.
First is the initial configuration using the console. The software used is 6.1 , sensor hardware is IPS 4235 . I am doing the config NOT running built-in #setup dialog.
Enjoy and have a nice day.
Yuri
Here is a feature that will save you time and frustration in many possible scenarios – especially when managing Cisco routers in multi-user environment. Once enabled archiving saves periodically copy of the running configuration of IOS router to the flash or remote server. So
next time something stops working after changes and you don’t know which one caused this – just revert back to the working configuration that is readily available.