* The video was shot in HD 1080p so make sure to enter the full screen.
* I put this video here as Youtube initially removed it for 'violation', most probably just because of the word 'crack' in its title, but after my talking with them the videos and channel are back so you can use them as well for all the videos Youtube channel
This crackme is of difficulty 1, that is not difficult at all. It is more like “Hello World” in the programming world – helps to learn the tools of the trade, familiarize with the process itself and finally give some motivation to continue the studies. So it does have a good educational value. Let’s have a look at the requirements:
Basically it asks to find the password inside the binary not dynamically tracing the program in any debugger (long live the SoftIce by Nu-Mega of course – it was the best debugger of its time, allowing even to do the driver/kernel debug, “ICE” in its name being in-circuit emulator, the lowest level possible). For this crackme I will be using HIEW hex editor. Being that simple we may solve it in so many ways, but let’s try just 3 of them.
- Find the correct password
- Do NOT use Soft Ice or any other debugger!
- You must use only a disassembler/Hex-editor
- Bonus: Patch the file so it doesn't matter what the input is
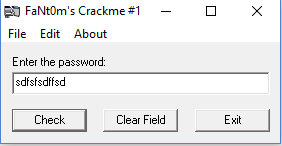
1) Tracing back in disassembly the error message. The usual way to solve simple crackmes is to run it, enter the wrong password, jot down the error message and put a breakpoint on the Windows API (like MessageBox/GetDlgItem) that produces this message, later to trace back to the function that decides whether the entered password was right or wrong. Here we are limited to disassembly only so let’s run the program entering some junk for a password:
And we get the error message:
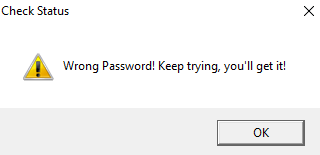
which we can (hopefully) find with the HIEW editor by using F7 , then F6 to find xreference where this string is being used in the code :
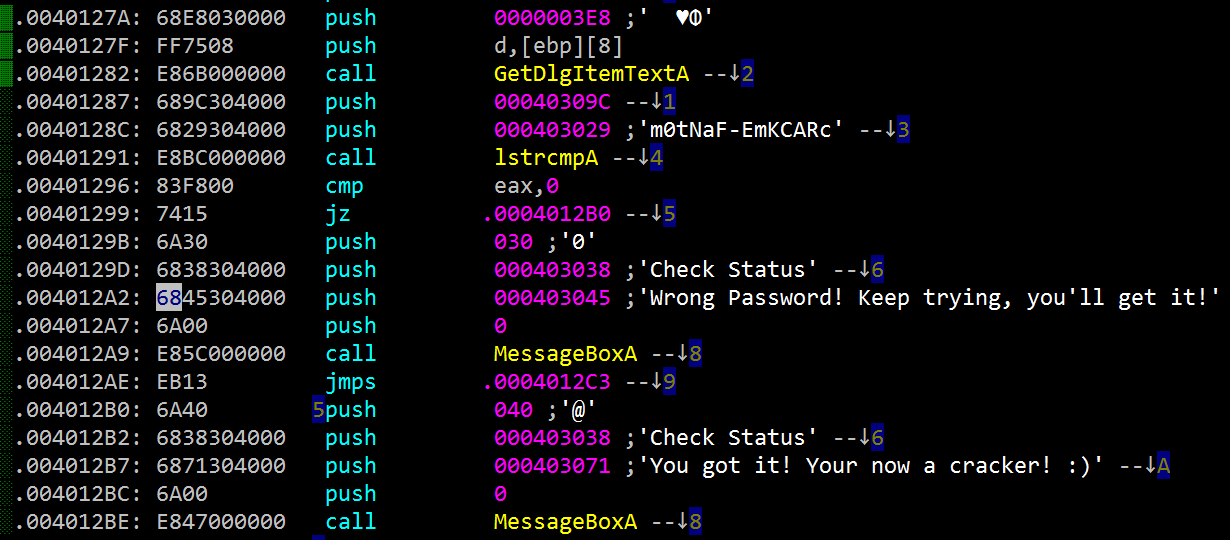 We find it on line 11 and if we look few lines above – line 8, there the decision is being made where to jump, to address .0004012B0 which contains the message “You got it! Your now a cracker” or, if jump doesn't happen, continue with the flow until our error message is printed. This decision by jz is based on result of a comparison done by the function at line 6 lstrcmpA – Windows API function to compare two strings, if they equal the EAX register is set to 0, in which case the cmp + jz opcodes send us to the successful message, if they are not we go to the error message. And what are the strings being compared? If we look at the line 5 we get one of them – our password 'm0tNaF-EmKCARc'. Оба-на, mission accomplished!
We find it on line 11 and if we look few lines above – line 8, there the decision is being made where to jump, to address .0004012B0 which contains the message “You got it! Your now a cracker” or, if jump doesn't happen, continue with the flow until our error message is printed. This decision by jz is based on result of a comparison done by the function at line 6 lstrcmpA – Windows API function to compare two strings, if they equal the EAX register is set to 0, in which case the cmp + jz opcodes send us to the successful message, if they are not we go to the error message. And what are the strings being compared? If we look at the line 5 we get one of them – our password 'm0tNaF-EmKCARc'. Оба-на, mission accomplished! 2) Looking at the .DATA section .
This method relies on the PE file format convention that all initialized and global data is placed in the file section .DATA . So let’s just see the sections of the file in HIEW by using F8 then F6 and here it is, starting at RVA .3000 we have this section.
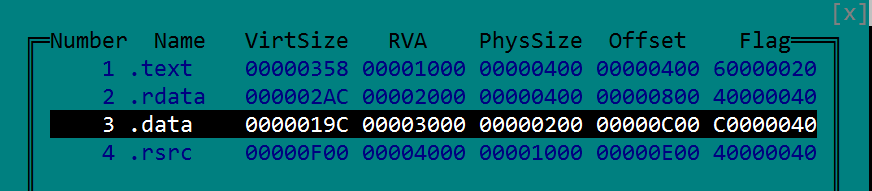 Hit enter to jump to the section and here we find all the programmer set data – namely the strings. One of them is our password:
Hit enter to jump to the section and here we find all the programmer set data – namely the strings. One of them is our password:
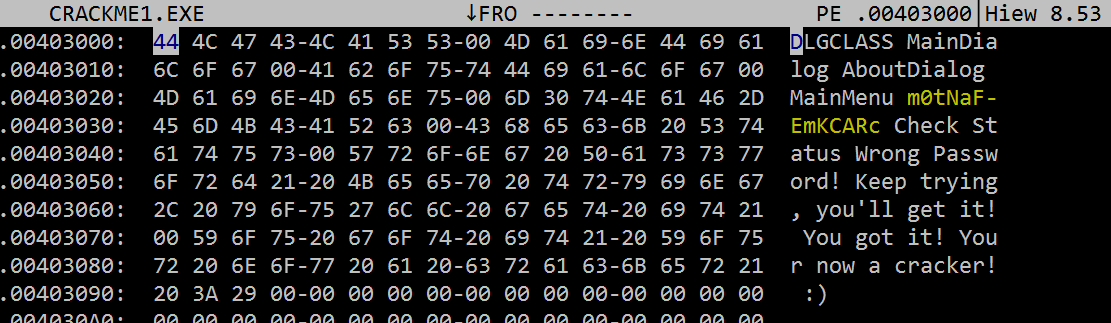 3) Just looking at all the strings
3) Just looking at all the strings The lack of string obfuscation in this binary allows us to just Alt + F6 to list all the strings and there we will see the password as well.