As most of the posts here this one is also inspired by a client. There was an unassuming shy and not making any troubles eSafe 8.5 appliance XG-200. Then one day Security Admin of the company complained to me about ‘high CPU utilization’ – getting somewhere up to 60% . eSafe looked absolutely fine and doing its work.
Also I noticed it was kinda working hard , nothing special but just general feeling that it handles a lot of load. And boy was I right – it was doing 200 Mb of logs per day . Given the number of stations in LAN and working hours that was huge. I looked with awk at the logs and happily updated the SecAdmin that eSafe is doing its work and blocks all the users trying frantically to visit various porno sites ignoring the “Site is blocked ..”message by the eSafe. “What? my users to pron sites, can’t be, can you show me the logs, who does it ?” . No problem, and so the awk one-liners you see below were written to parse esafe Aladdin logs to get some insight. Also at the end of the post see eSafe log format in case you want to develop your own scripts.
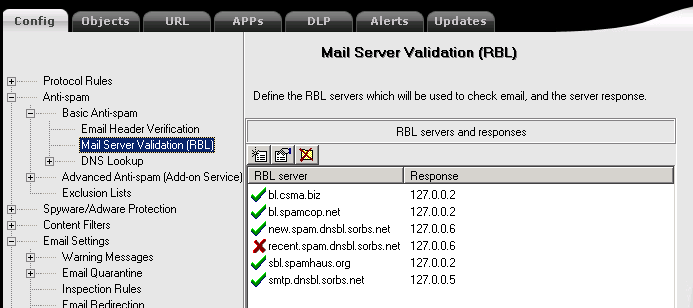
All logs are located at /opt/eSafe/eSafeCR/SessionLog/
One-liner number one – Gather IPs that sent spam , count number of spam messages per IP, sort the list in ascending order .
32 41.59.0.205
41 74.63.80.6
41 83.16.167.14
48 125.163.188.31
54 125.163.192.184
57 113.168.9.224
78 89.223.56.16
80 212.143.70.26
104 212.143.70.27
One-liner number two – Mail sender fileds of spam messages , just for fun , no real value for security purpose:
10 bsb@bsbinfo.in
13 info@all-free.co.il
13 Janette@2.90.58.204
15 Ronnie@178.34.19.174
17 KellieClements@cramerspointmotel.com
22 notifs@m.snapinteractiveapps.com
60 ezrachmudag26@gmail.com
25 Simone@187.63.223.21
102 Angelo@31.subnet125-163-188.speedy.telkom.net.id
One-liner to see all the blocks/rejects reasons and respective statistics.
21967 File allowed
360 File blocked
114891 File clean
1731 File modified to remove malicious content
3650 Mail clean
111 Mail modified to remove malicious content
13 Mail rejected #912 – Anti-spoofing – Mail rejected. Attempt to impersonate a local user
164 SMTP error
803 Spam blocked
Now let’s move to HTTP browsing.
One-liner number four – blocked access to websites : number of blocked attempts per website, hostname of the website, internal LAN IP of PC that tried to access the resource.
I do not bring examples here as they are quite embarrassing, even to be brought anonymously, so just trust me – run it on your esafe and you will blush.
Same as above but with full path to the prohibited file.
And finally as promised the format of eSafe logs. All the fields in logs are separated by vertical bar (as you probably guessed awk –F”|” accounts for that). All the fields are present, while irrelevant fields are empty. So it is really scripting-friendly. I broke down the fields into separate lines with field number of each field. Enjoy.
2 eSafe name
3 Record ID
4 ProtocolType
5 Method
6 Event
7 URL host
8 File Name\Mail Subject
9 File Type
10 #File Size
11 Source IP
12 Destination IP Continue reading