Recently I was unplesantly presented with “it is not a bug ,it is a feature” case with the Checkpoint .
There was some UTM with TS (Total Security) valid license that includes antivirus and antispam services that client paid for and even asked to enable. So far so good. Part of the routine I checked on Gateway properties Antivirus and Antispam features , in Content inspection picked this UTM as enforcing Antispam/Antivirus policy , did install and .. got a call from the client that they can’t send/receive mails . In SmartView Tracker I saw the error of invalid license (it was the most clever disguise Checkpoint could come up with) , on command line fw monitor proved connections to port 25 arrive perfectly and pass pre/post insert points inbound but then nothing happens. Trying to telnet port 25 to the external ip of the mail server got me opened session , then connection was reset.
Only with the help of Checkpoint support (that actually were surprised that after all these years with their
product I haven’t seen this “feature” yet) did I find that issue is known one and caused by that to represent the mail server in LAN I created a MANUAL NAT rule . And ANY security server inside Checkpoint has to
know from security rules or from object properties its ip before and after NAT. Of course this info is
not to be located in any guides.
So to fix the situation you have to either :
- replace manual NAT rules with automatic ones;
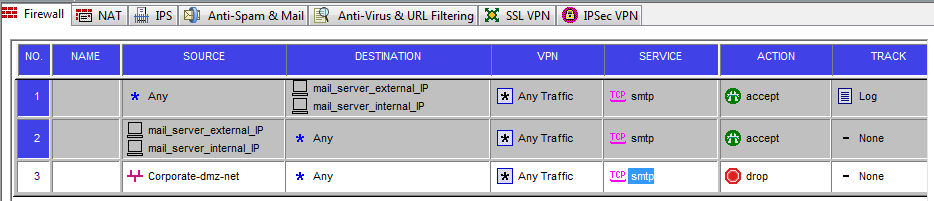
- in security rules relevant to the server in question use BOTH internal and external IPs (that was
what I did and it works ever since – see screenshot below).
I did the rules similar to this:
NB there exist Secureknowledge base articles for it :
sk34862
sk32198
PS I talk here about SMTP but enabling Antivirus for the webserver in LAN with static NAT will have the same
devastating result.