Fortiweb Cookbook: Most Basic Setup - One website, add HTTPS support, Round Robin load balancing between two physical servers, all protections on Alert only, Host header filtration
Task: Taking the basic setup a step further, let's enable HTTPS protocol between clients and Fortiweb for the yurisk.com.
Solution.
Step 1. Create certificate signing request (CSR) to use in issuing the SSL certificate.
I will use Ubuntu server. It does not have to be a server actually hosting the website yurisk.com as long as I have the private key used in generating this CSR file.
Here I create a private key yurisk.com.priv.key and CSR yurisk.com.request.csr. While you can produce the private key file unencrypted by adding -nodes option, it is highly discouraged in production as anyone with this key can impersonate the SSL certificate of the website.
openssl req -newkey rsa:2048 s -keyout yurisk.com.priv.key -out yurisk.com.request.csr
Generating a RSA private key
................................................+++++
..............................................................................................+++++
writing new private key to 'yurisk.com.priv.key'
Enter PEM pass phrase:
Verifying - Enter PEM pass phrase:
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:IL
State or Province Name (full name) [Some-State]:Jerusalem
Locality Name (eg, city) []:Jerusalem
Organization Name (eg, company) [Internet Widgits Pty Ltd]:Yurisk Ltd
Organizational Unit Name (eg, section) []:IT
Common Name (e.g. server FQDN or YOUR name) []:yurisk.com
Email Address []:yuri@yurisk.com
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
root@ubuntu1:~#
Now I can use yurisk.com.request.csr to issue the SSL certificate. For this lab I used instantssl.com to get a free 30-day certificate, but of course any SSL CA provider will do. Once issued, I downloaded the ready-to-use certificate as a file yurisk_com.crt and can move to step 2.
Step 2. Import SSL certificate and potentially intermediate certificates into Fortiweb.
System -> Certificates -> Local -> Import ....
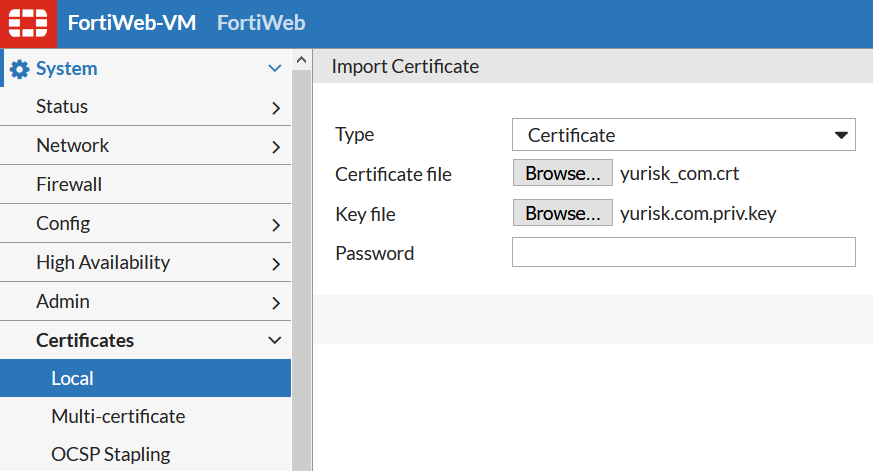
I use here the password set when generating the private key earlier on Ubuntu server.
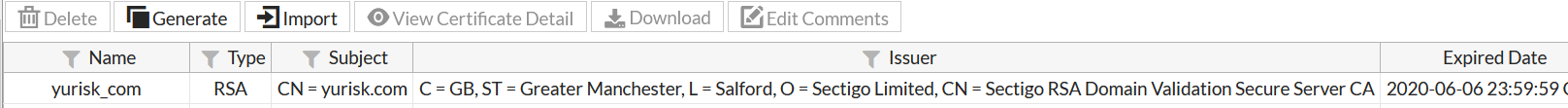
The result looks like:
Step 3. Enable the HTTPS service and set the SSL certificate to use in Server Policy.
Policy -> Server Policy -> Edit ....
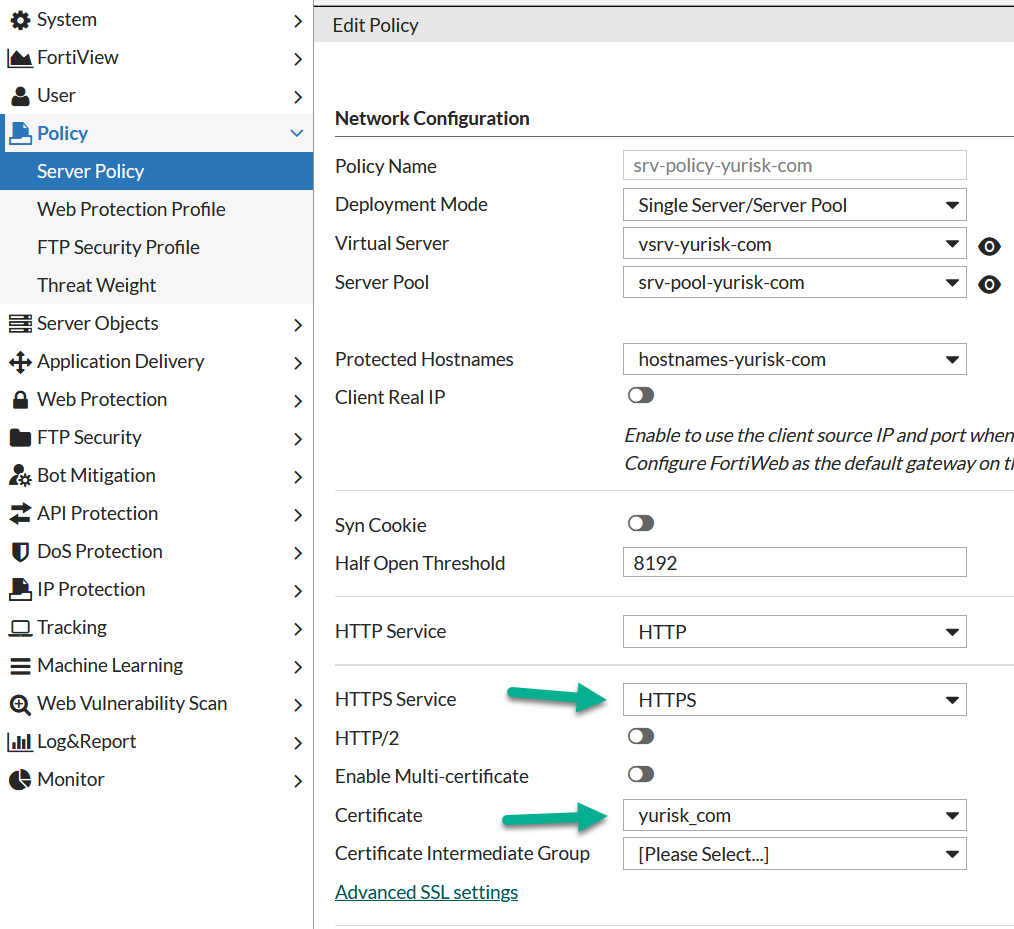
NOTE: I did not enable HTTPS or change the configuration of the Apache servers at all. The conneciton between Fortiweb and Apache servers stays cleartext on port 80. This is called SSL offloading - all the SSL related encryption/decryption is being done by the Fortiweb only, to offload these tasks from physical servers.
It is possible of course to enable SSL connection also between Fortiweb and internal servers.
Verify
For verification let's enter the https://yurisk.com. Also, to make sure the policy just Alerts, not blocks attacks, I will run dirbuster against the website.
Follow me on https://www.linkedin.com/in/yurislobodyanyuk/ not to miss what I publish on Linkedin, Github, blog, and more.